Keycloak
Resume
Single Sign On
URL: https://login-dev.cenabast.gob.cl/admin/
KEYCLOAK_USER: admin
KEYCLOAK_PASSWORD: owwIZLI#6m65
👉 Check Keycloak docker-compose.yml.
👉 Keycloak image is build from file Dockerfile.keycloak
Keycloak user & database
The first time Keycloak is deploy, a keycloak user and role must be created in the postgres database.
The password must match the password of KC_DB_PASSWORD at the Dockerfile.keycloak.
CREATE ROLE keycloak;
CREATE USER keycloak WITH PASSWORD 'password';
GRANT ALL PRIVILEGES ON DATABASE keycloak to keycloak;
GRANT ALL PRIVILEGES ON ALL TABLES IN SCHEMA public TO keycloak;
GRANT ALL ON SCHEMA public TO keycloak;
Keycloak Setup
After Keycloak docker is deployed, the following configurations needs to be done in order to integrate with Clave Unica.\
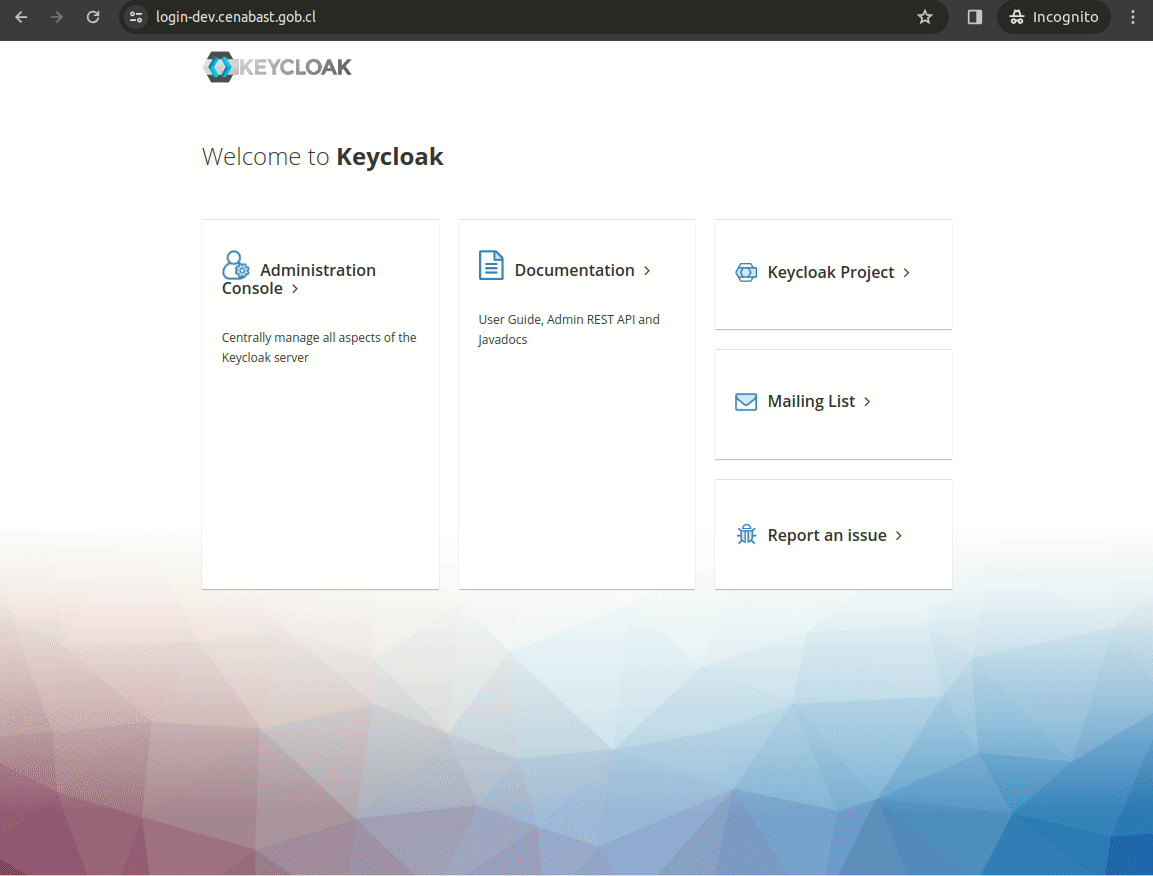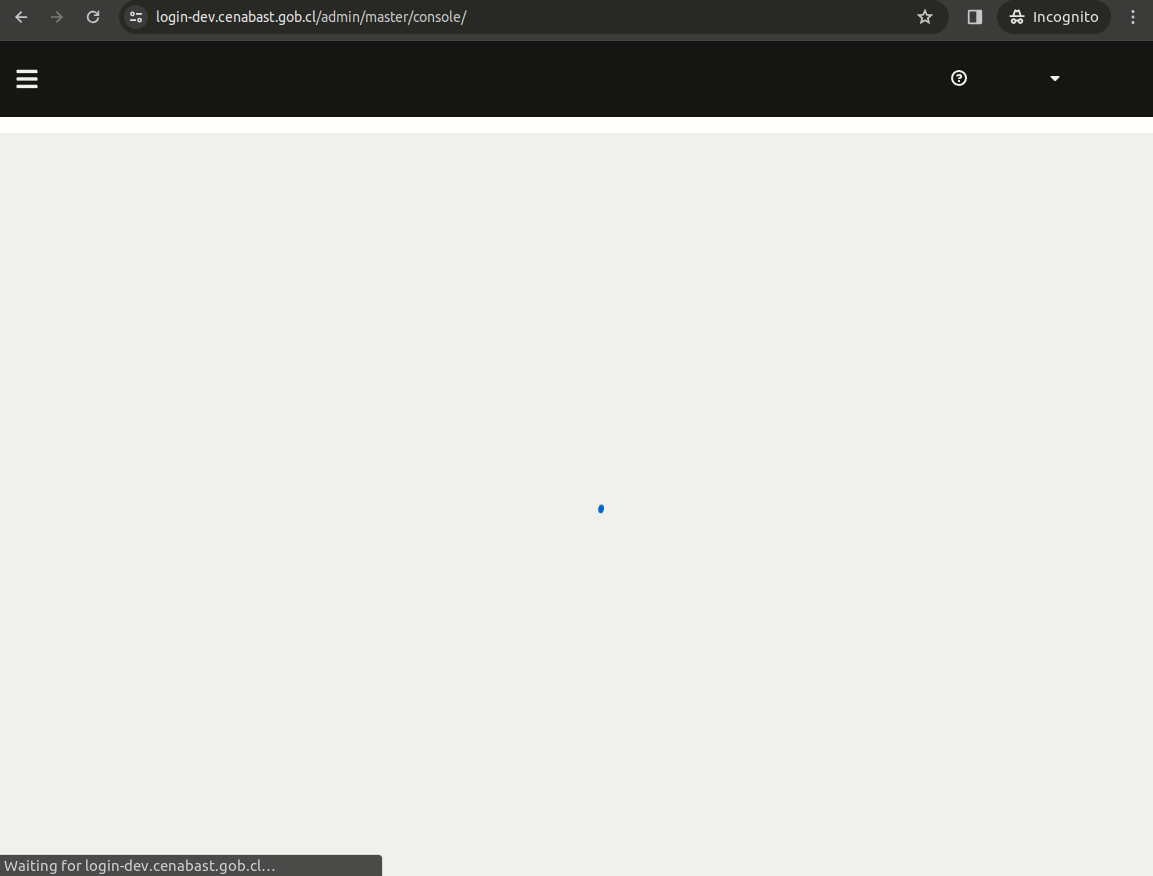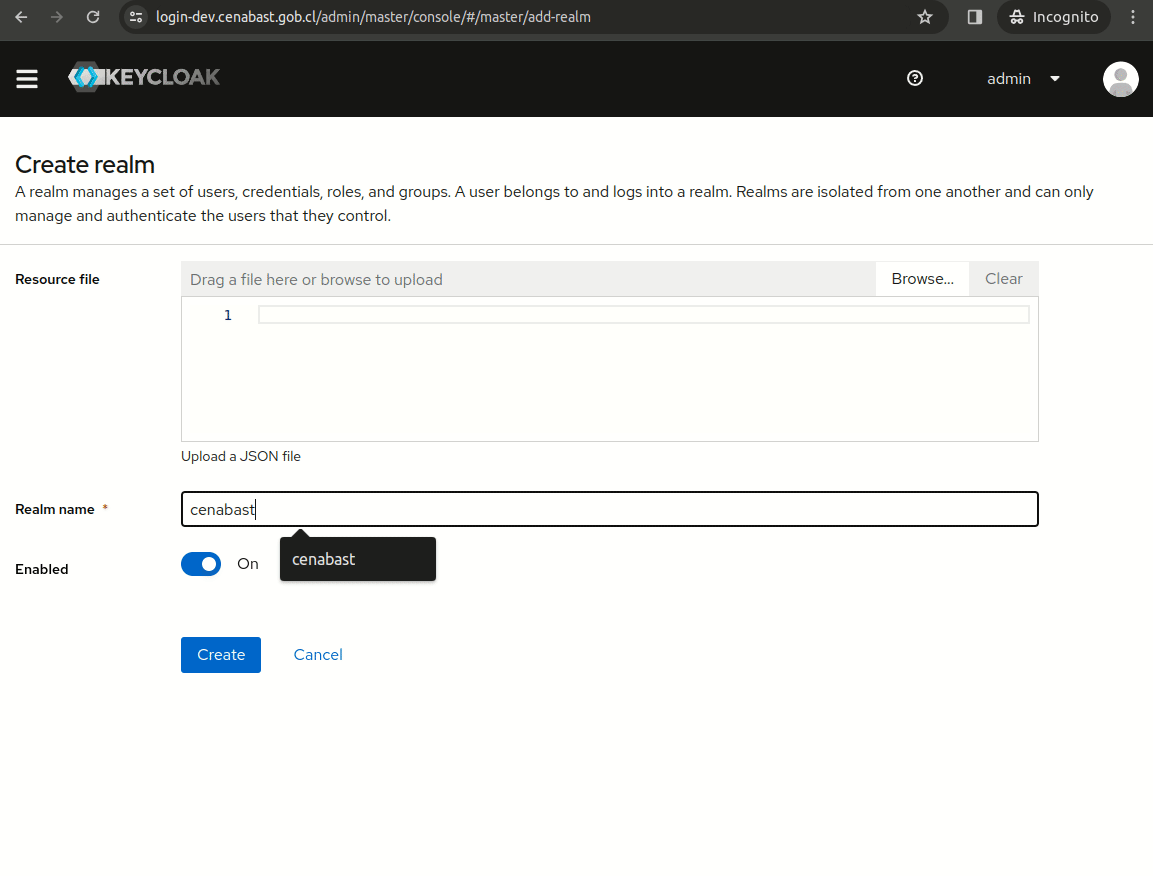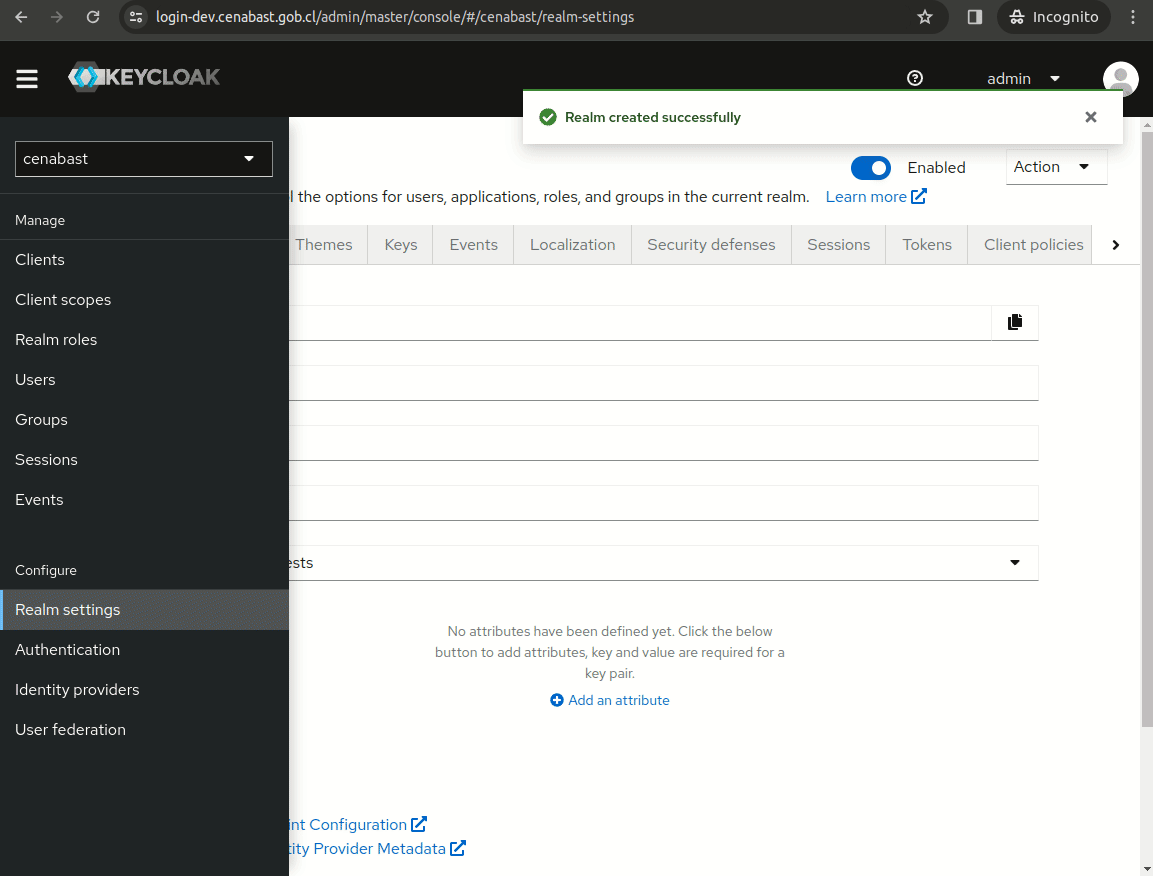
Create Cenabast Realm
Create a new realm:
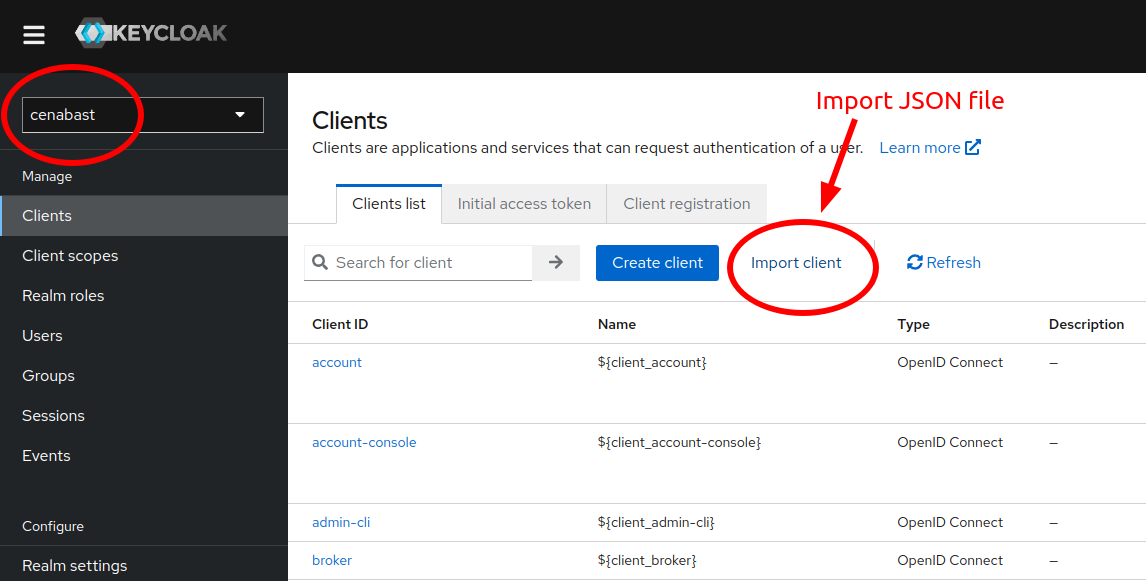
Create "cenabast-ecommerce" client
The initial OIDC client configuration can be imported using the following file cenabast-ecommerce.json.
The client value must match the KEYCLOAK_CLIENT_ID in the .ENV file.
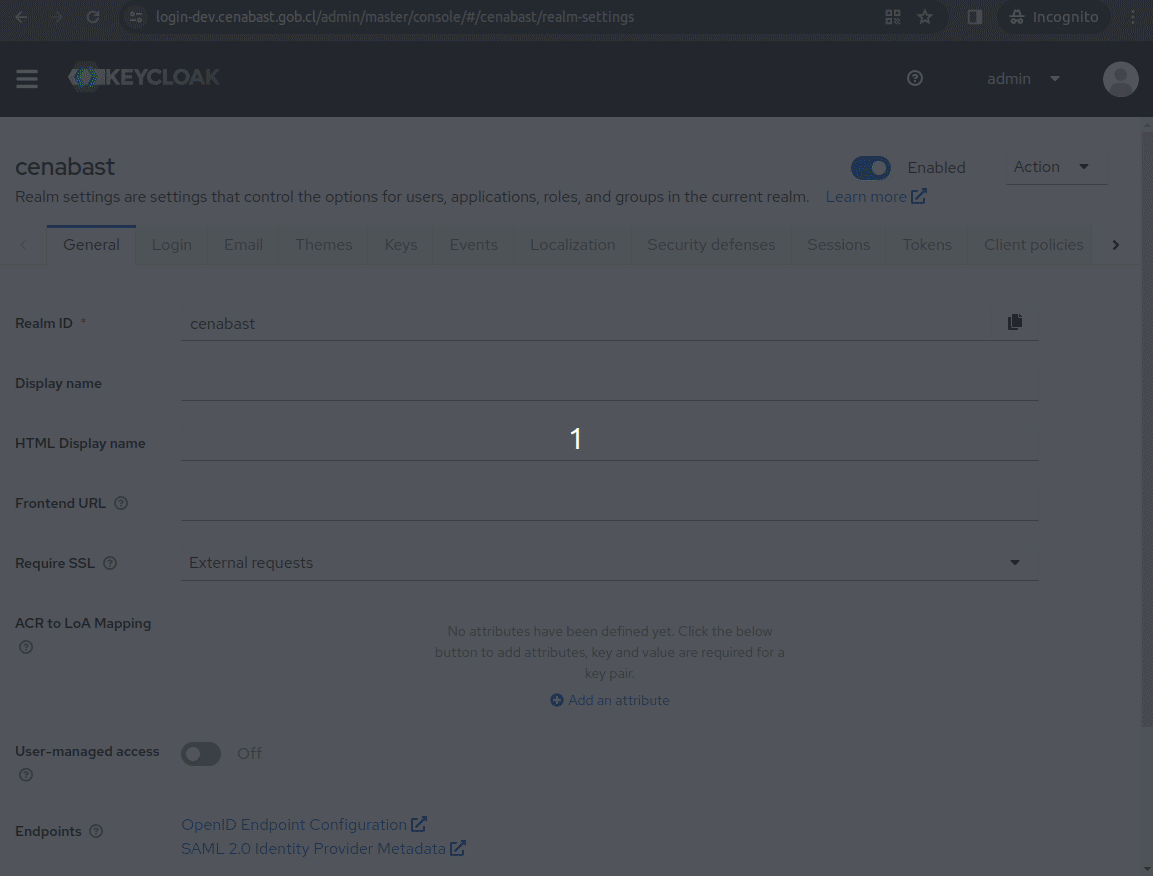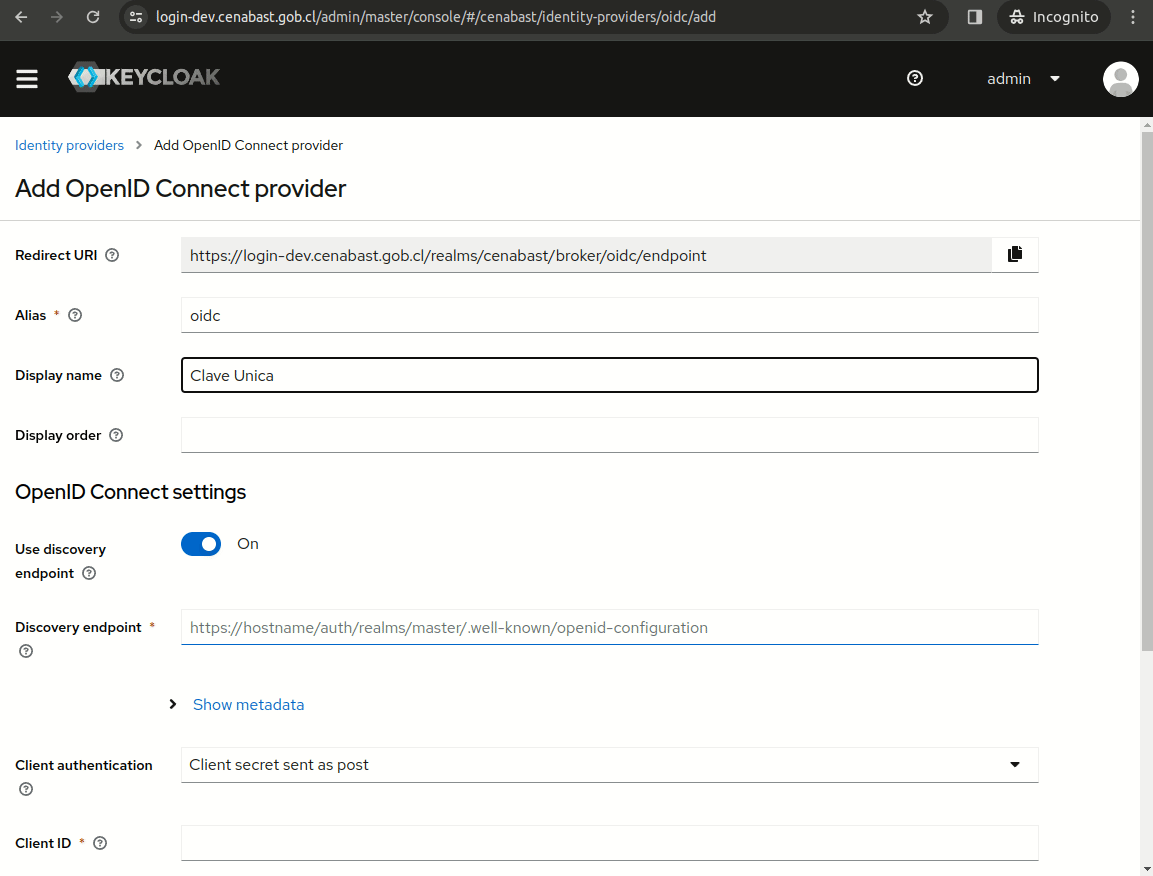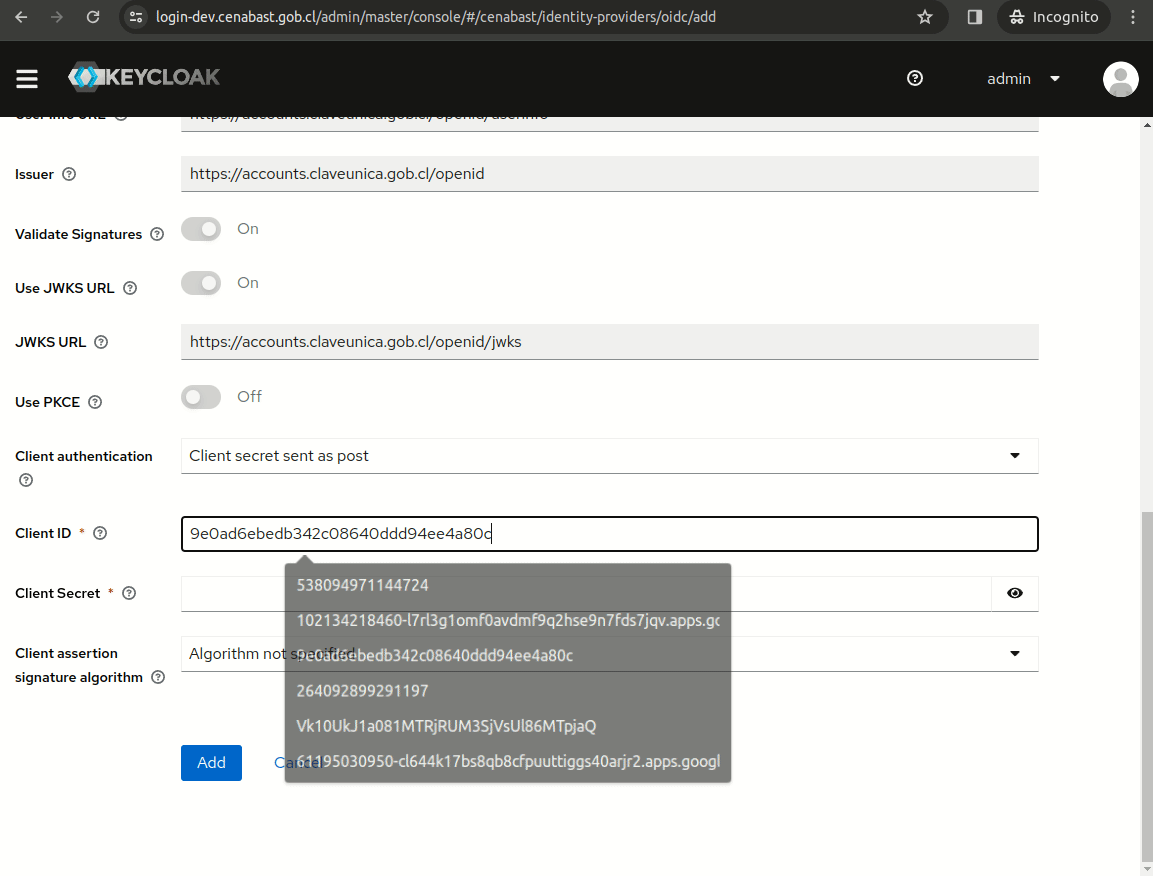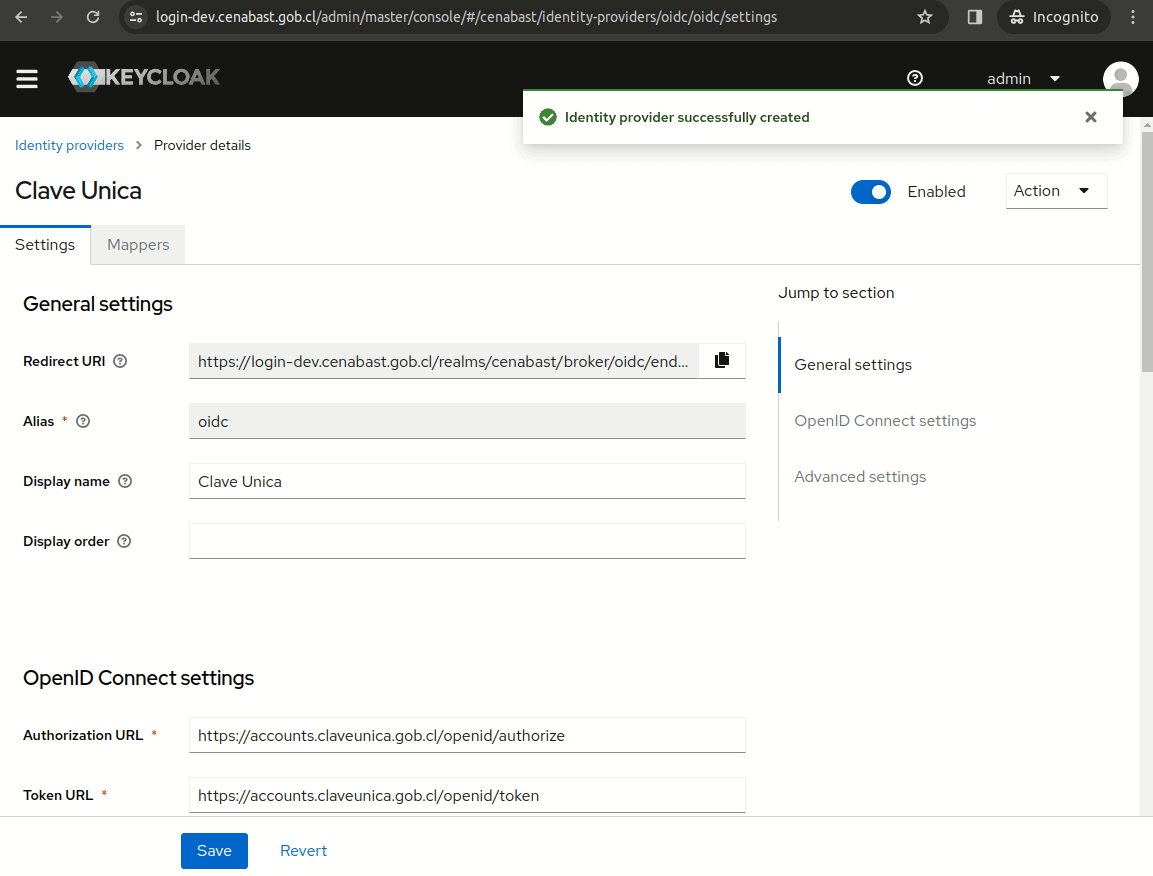
Create Clave Unica IdP
Clave Unica Discovery Endpoint:
https://accounts.claveunica.gob.cl/openid/.well-known/openid-configuration
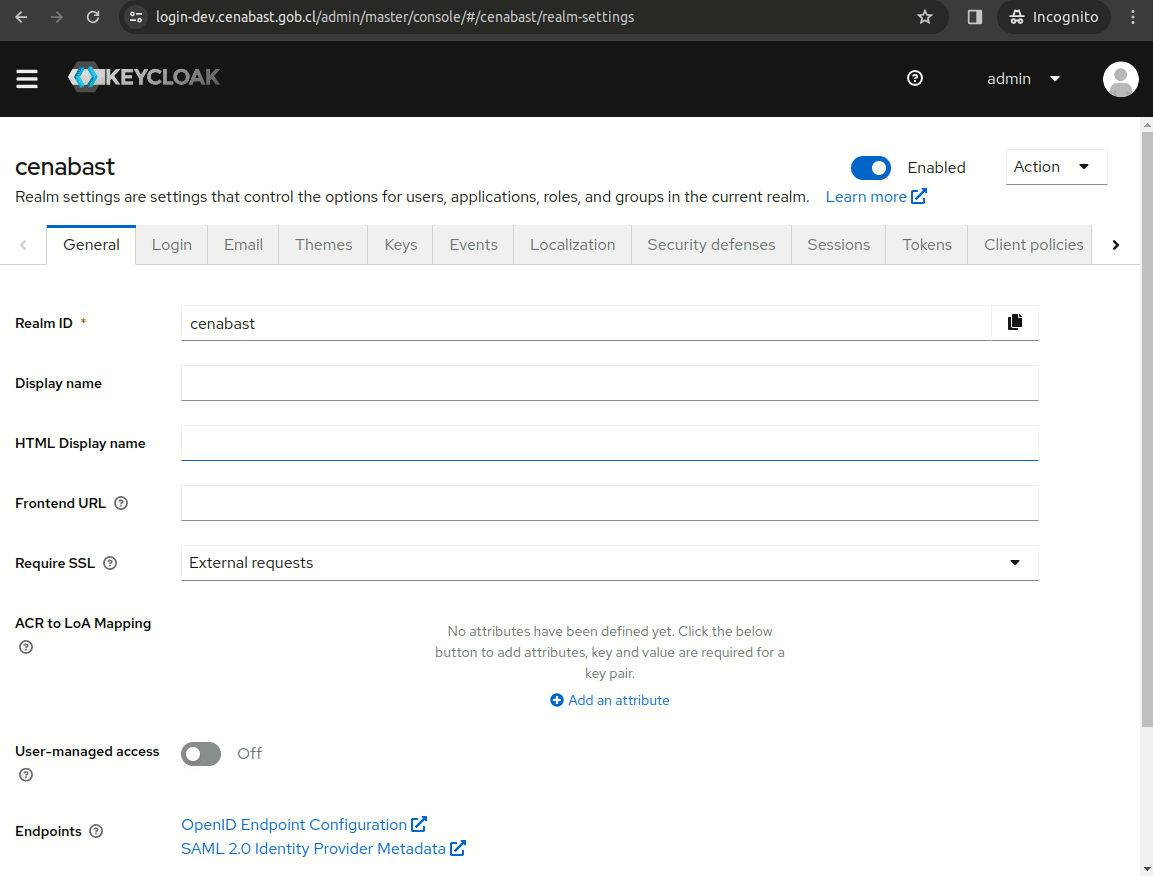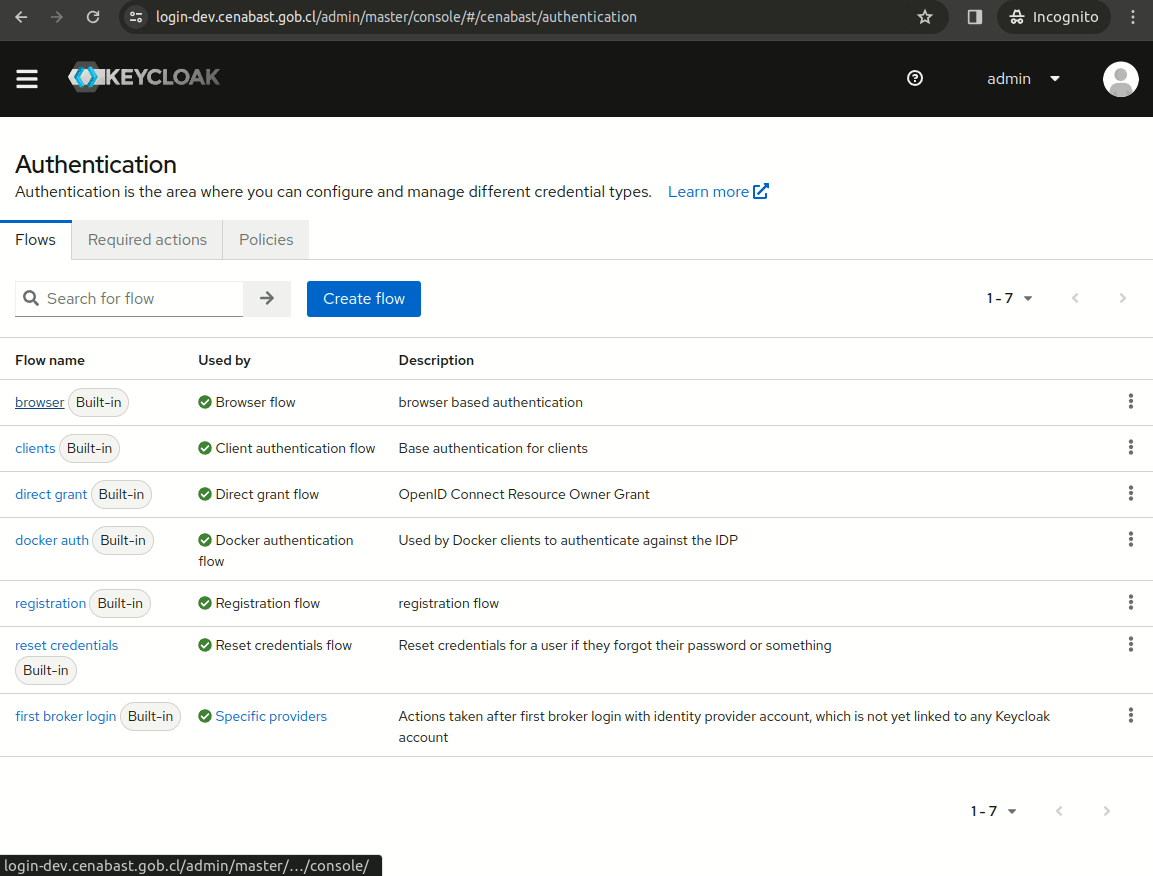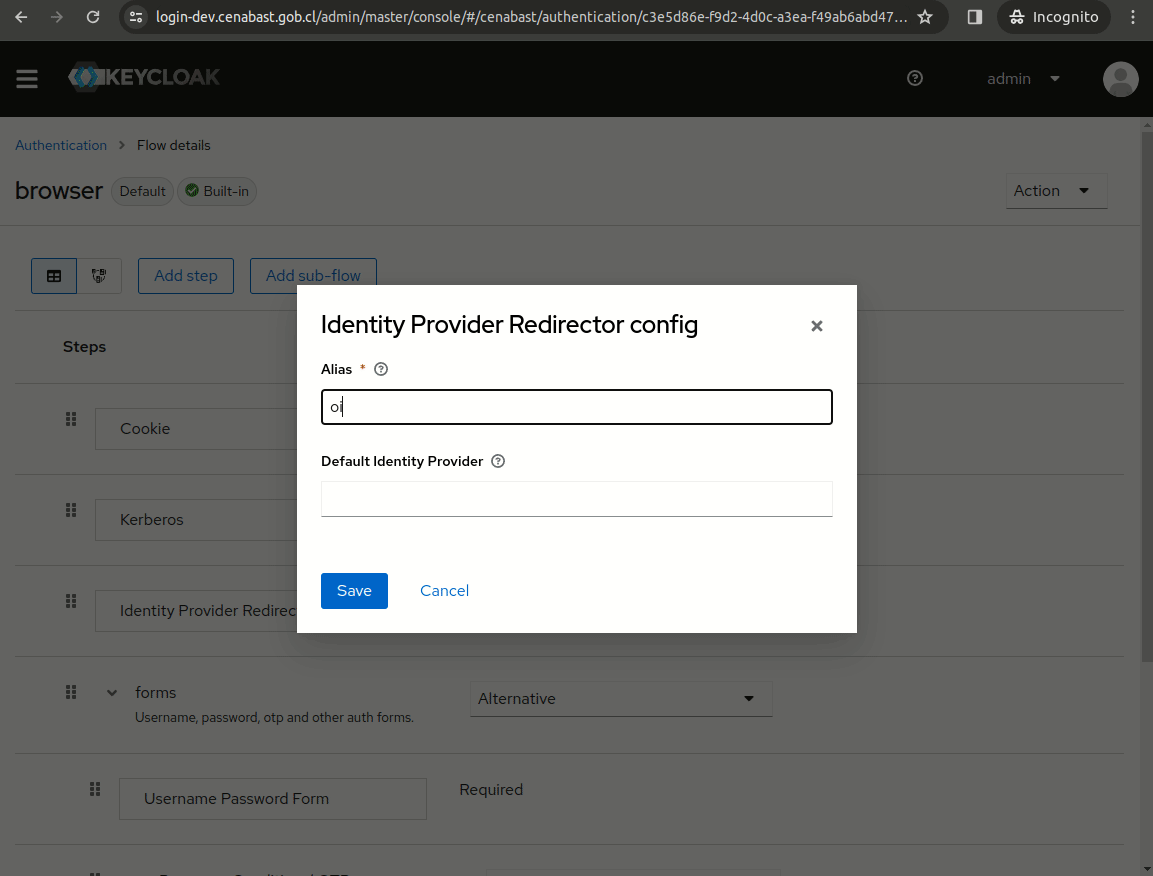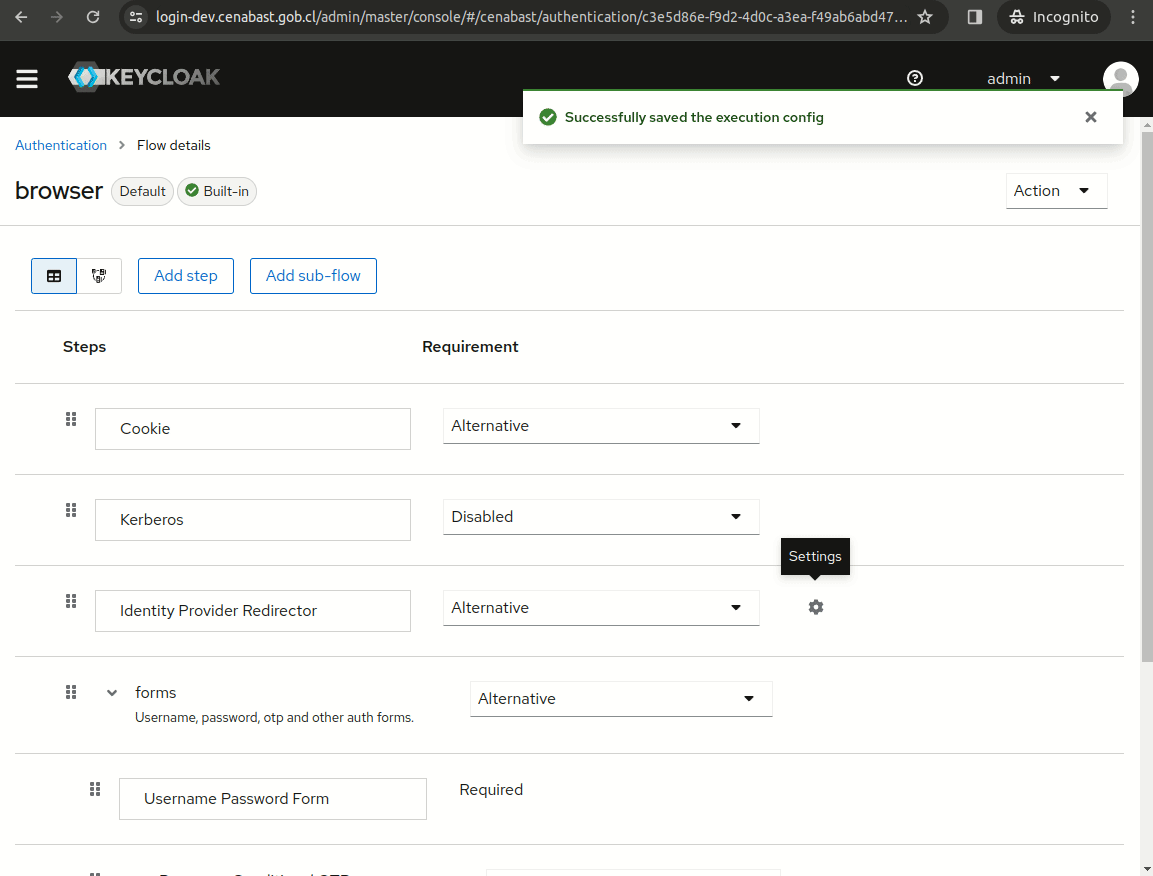
Redirect directly to IdP
In order to skip Keycloak Login form, we can redirect inmediatly to the ClaveUnica Identity Provider.
In the browser authentication flow, just configure the alias of your idp (in this case, "oidc" is the alias)
Disable Review Profile
Disable the "Review Profile" action from the "first broker login" flow.
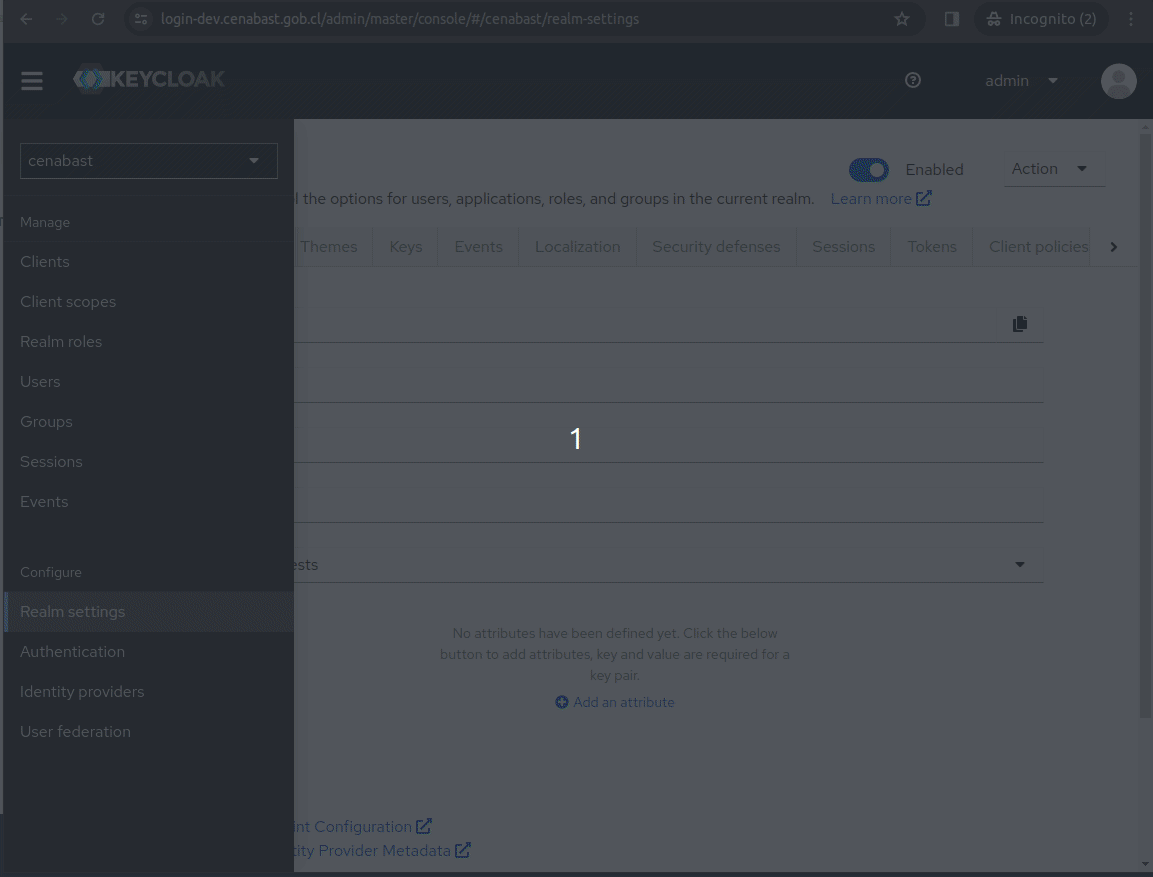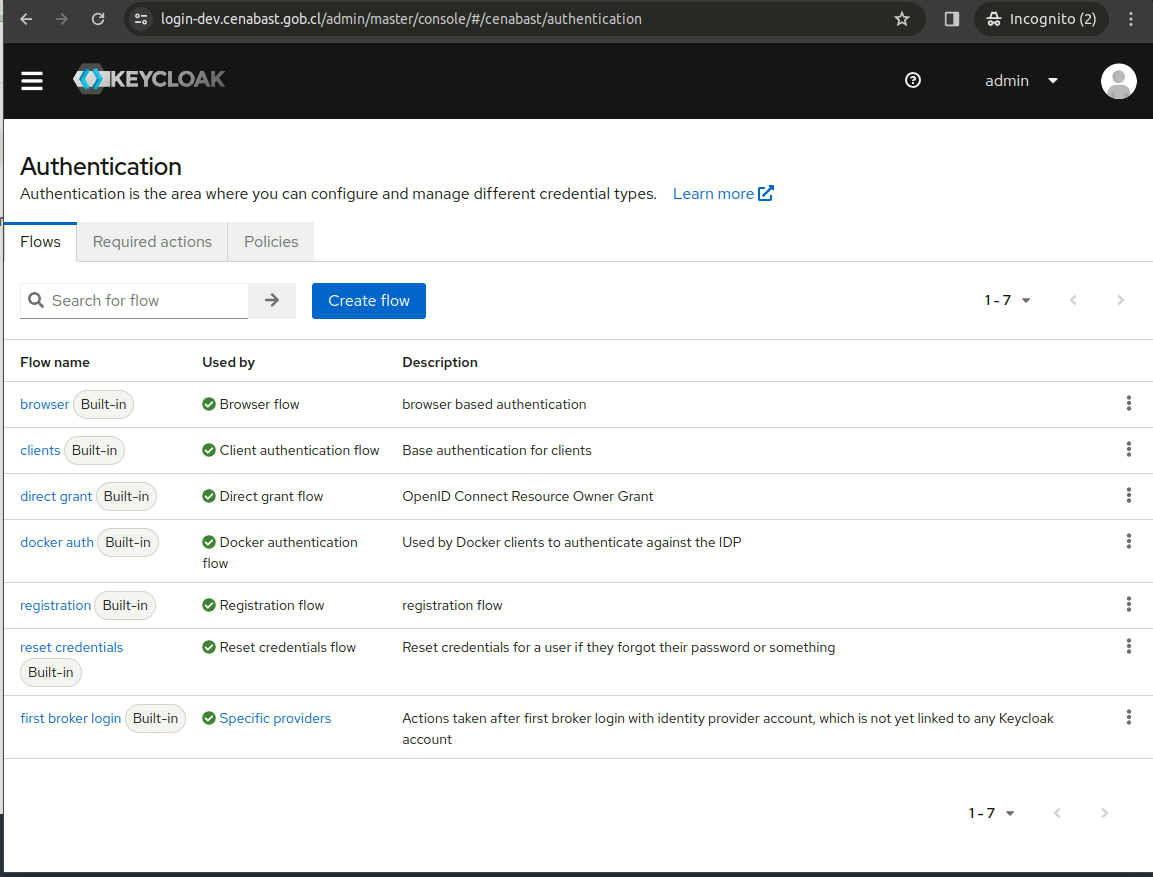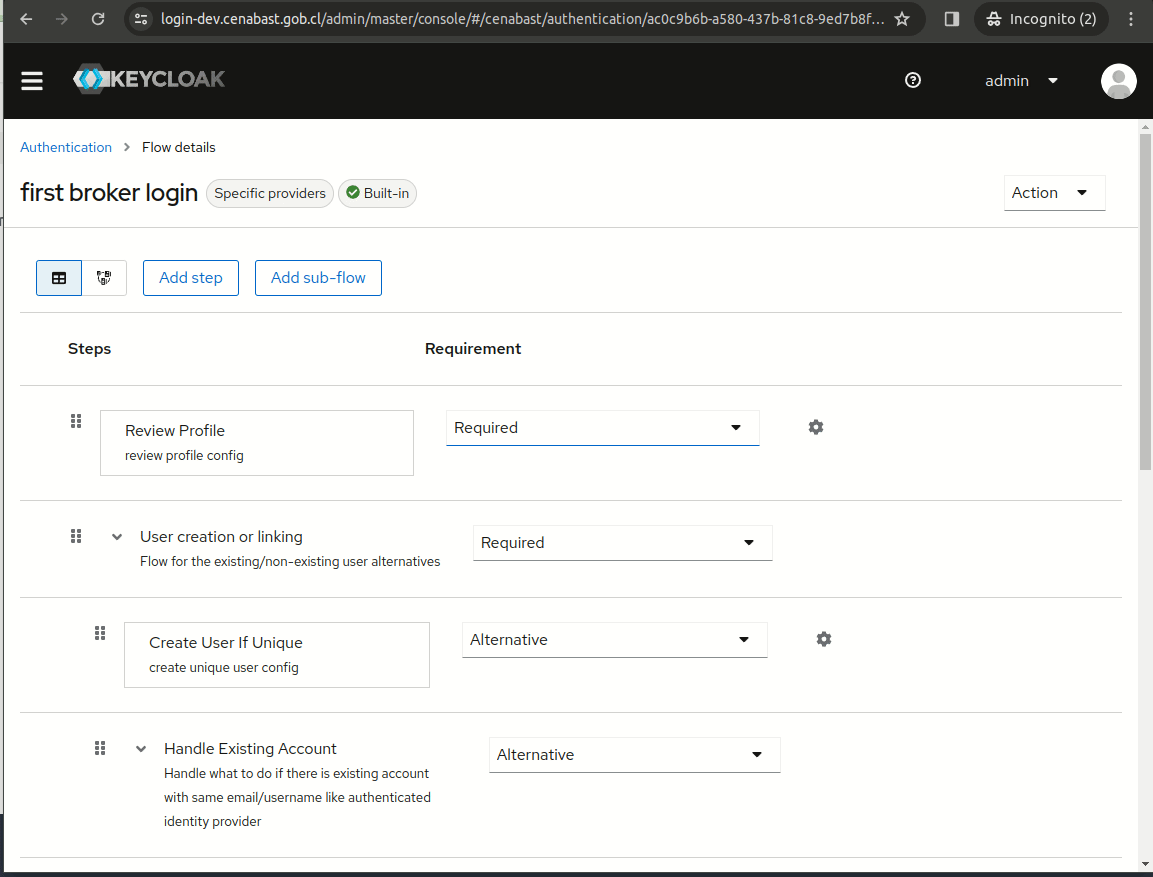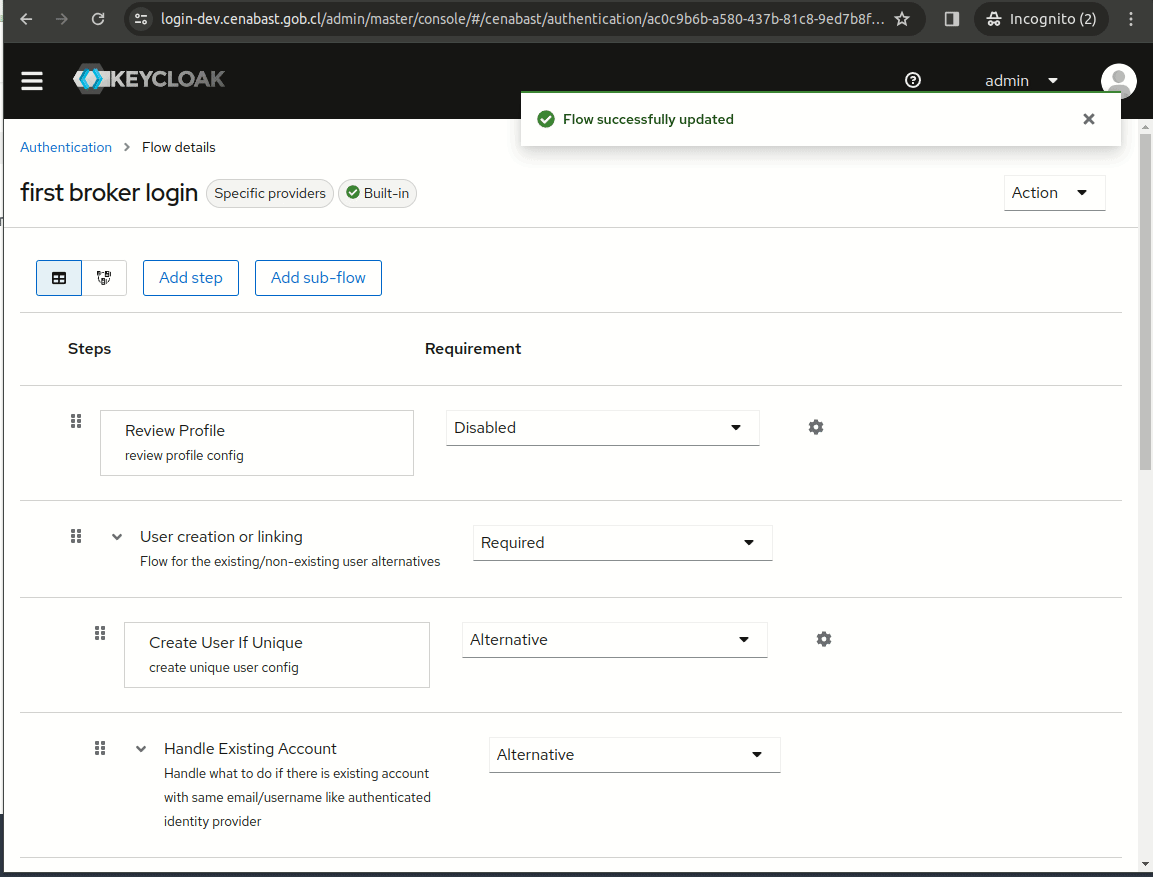
Disable Profile form
In order to prevent Keycloak from requesting filling the profile form, we need to disable the "Update Profile" required action.
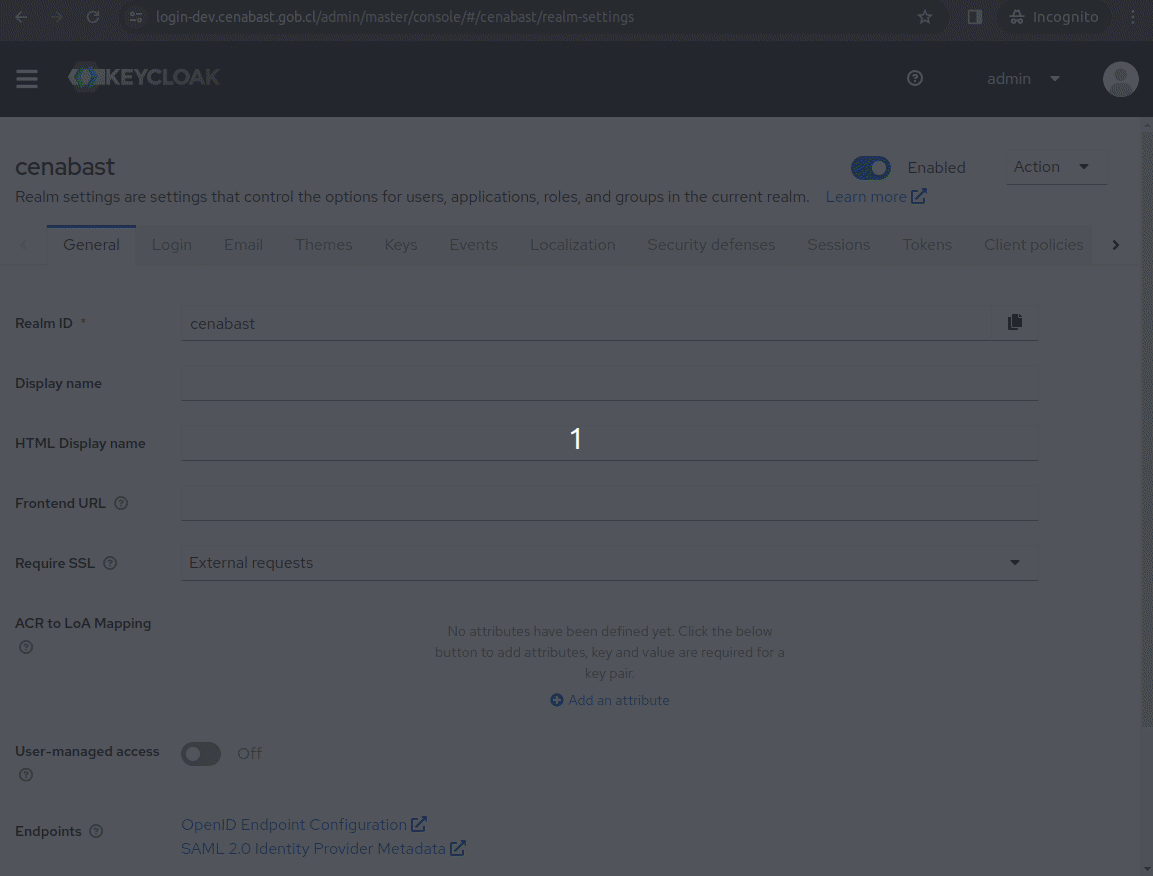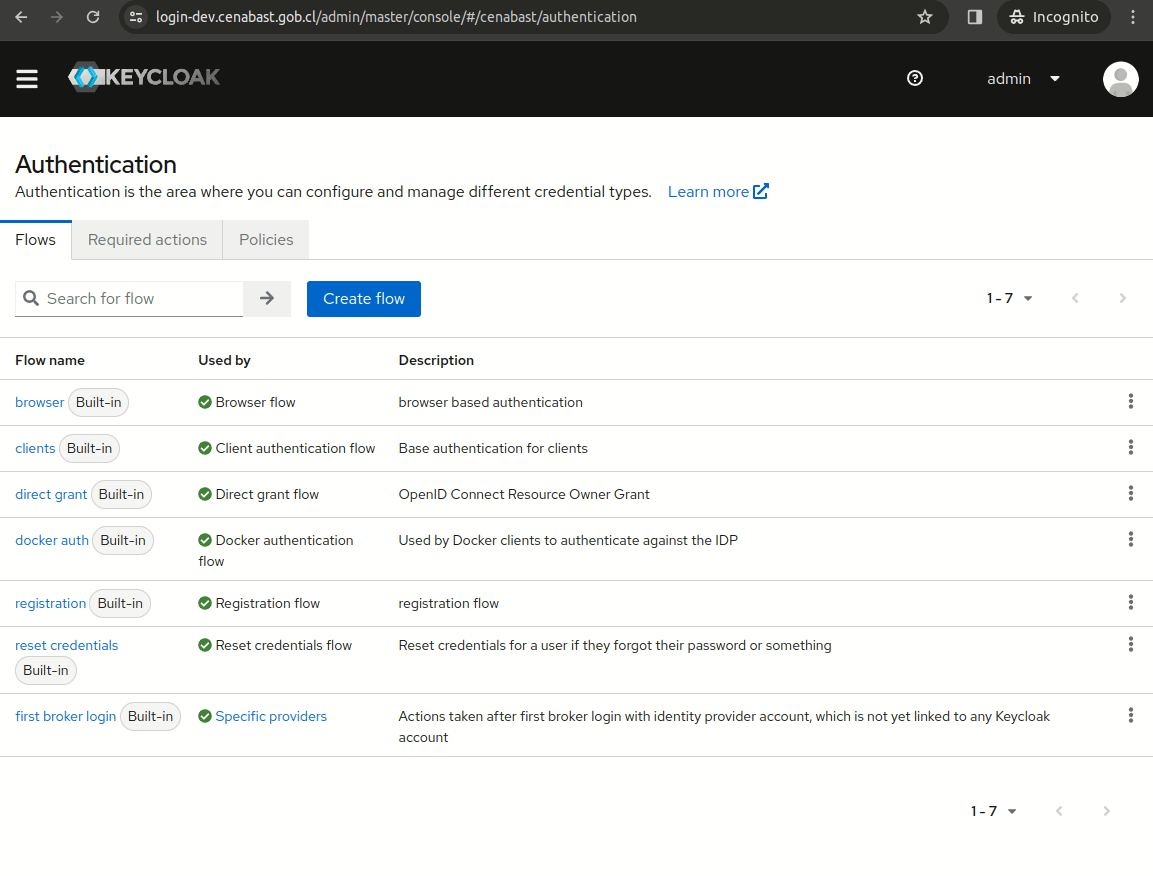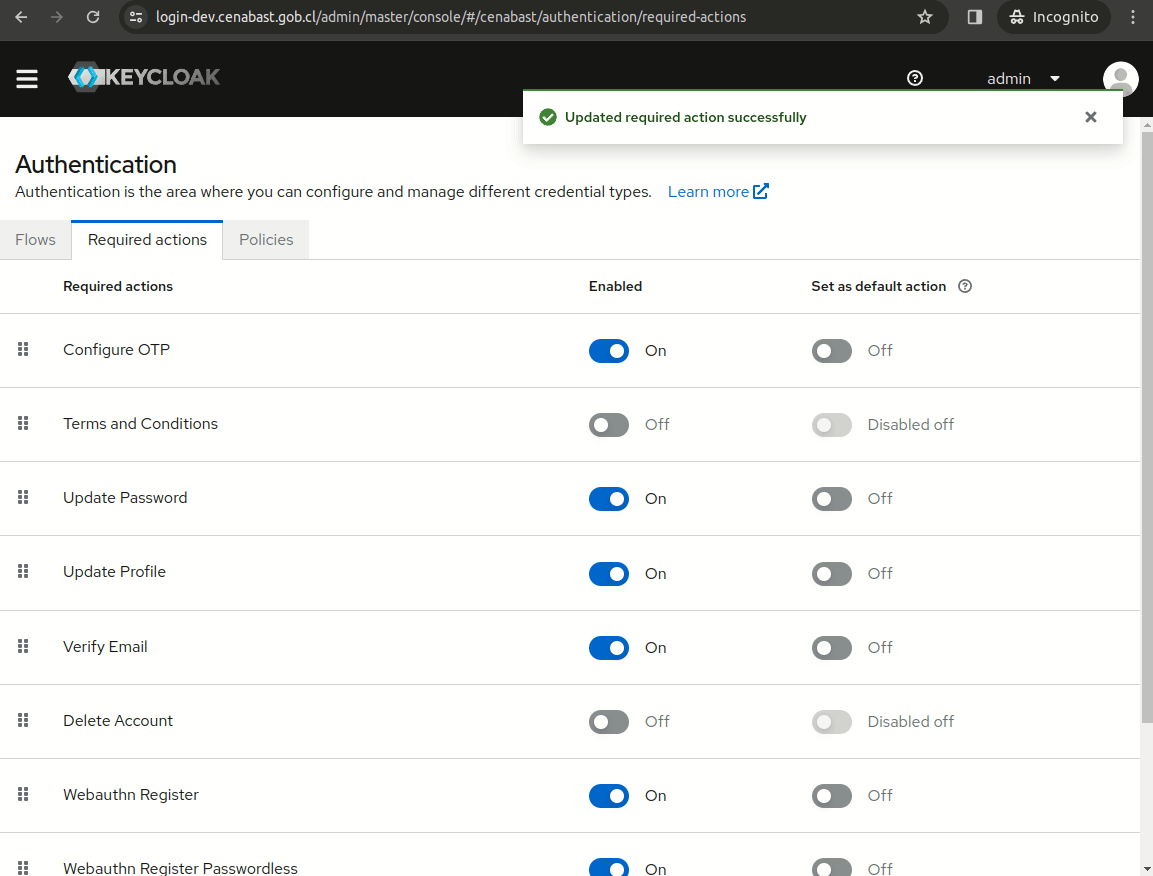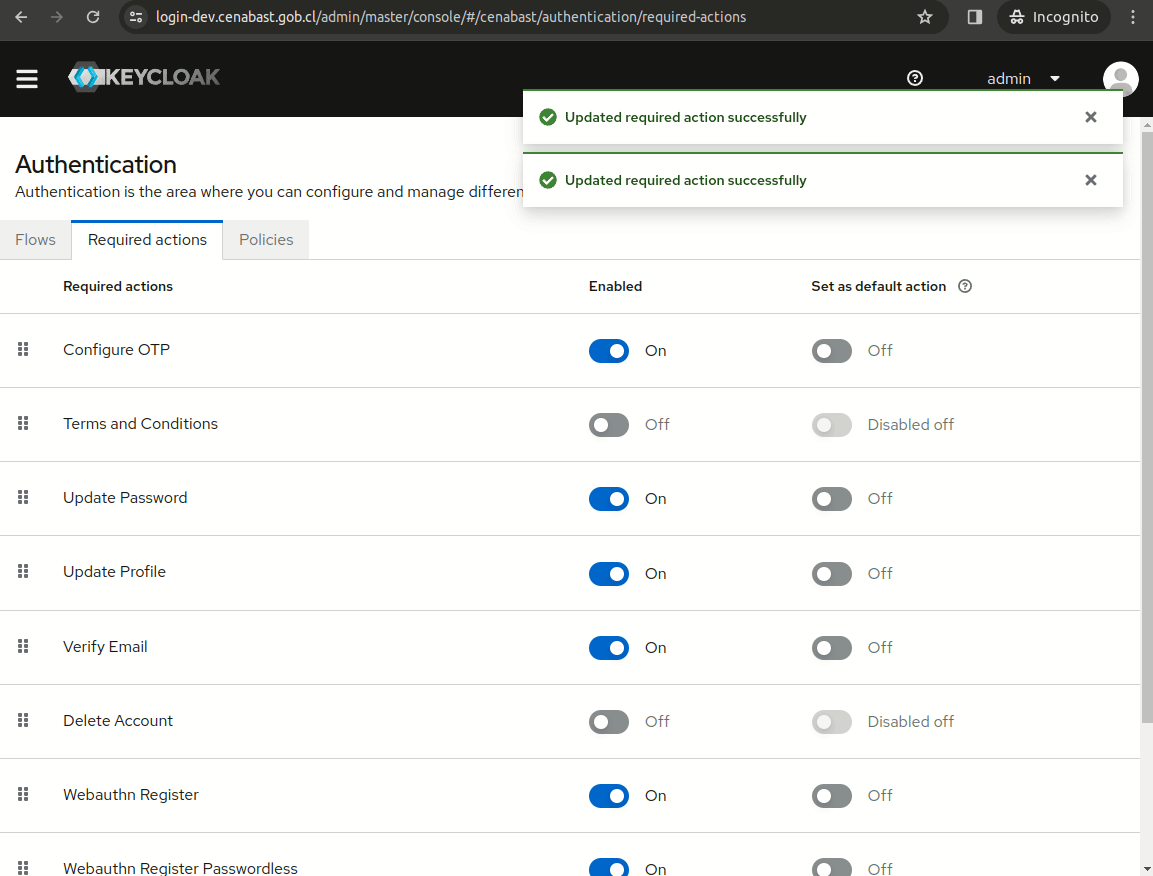
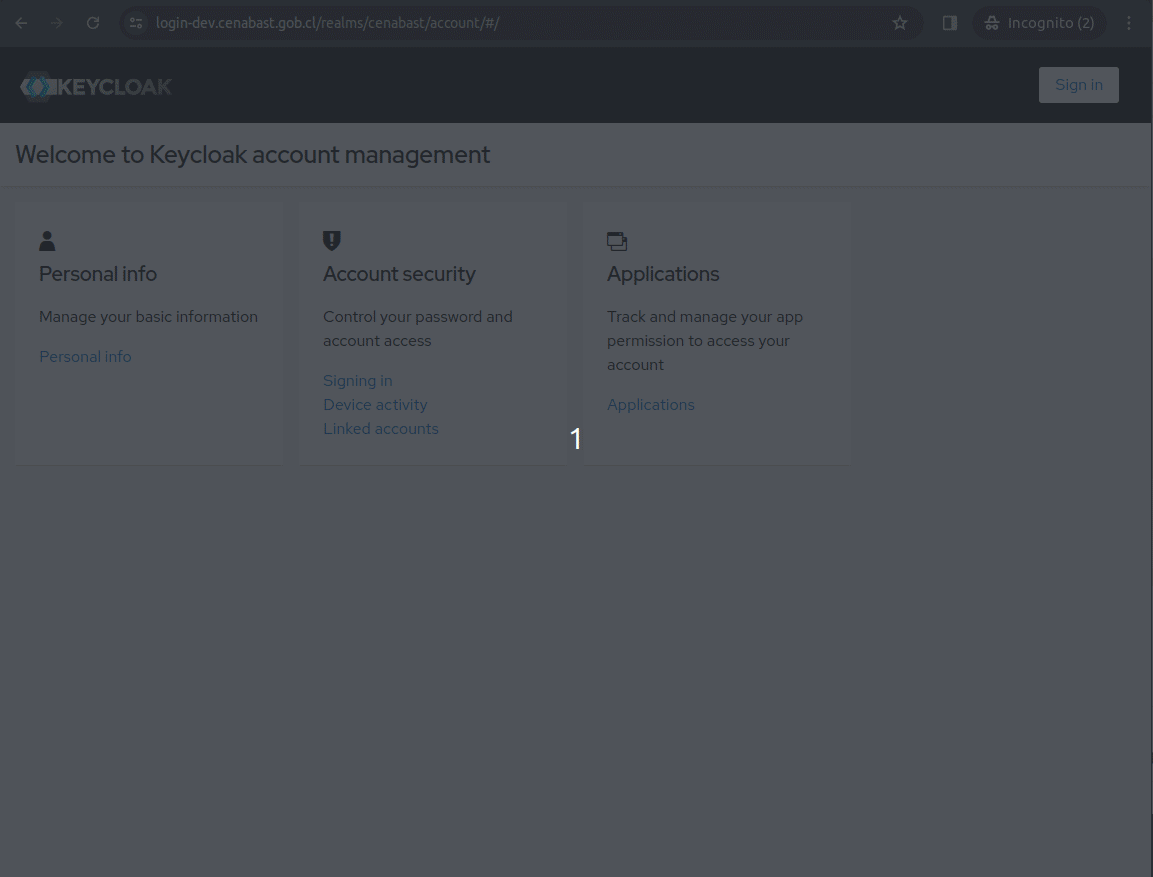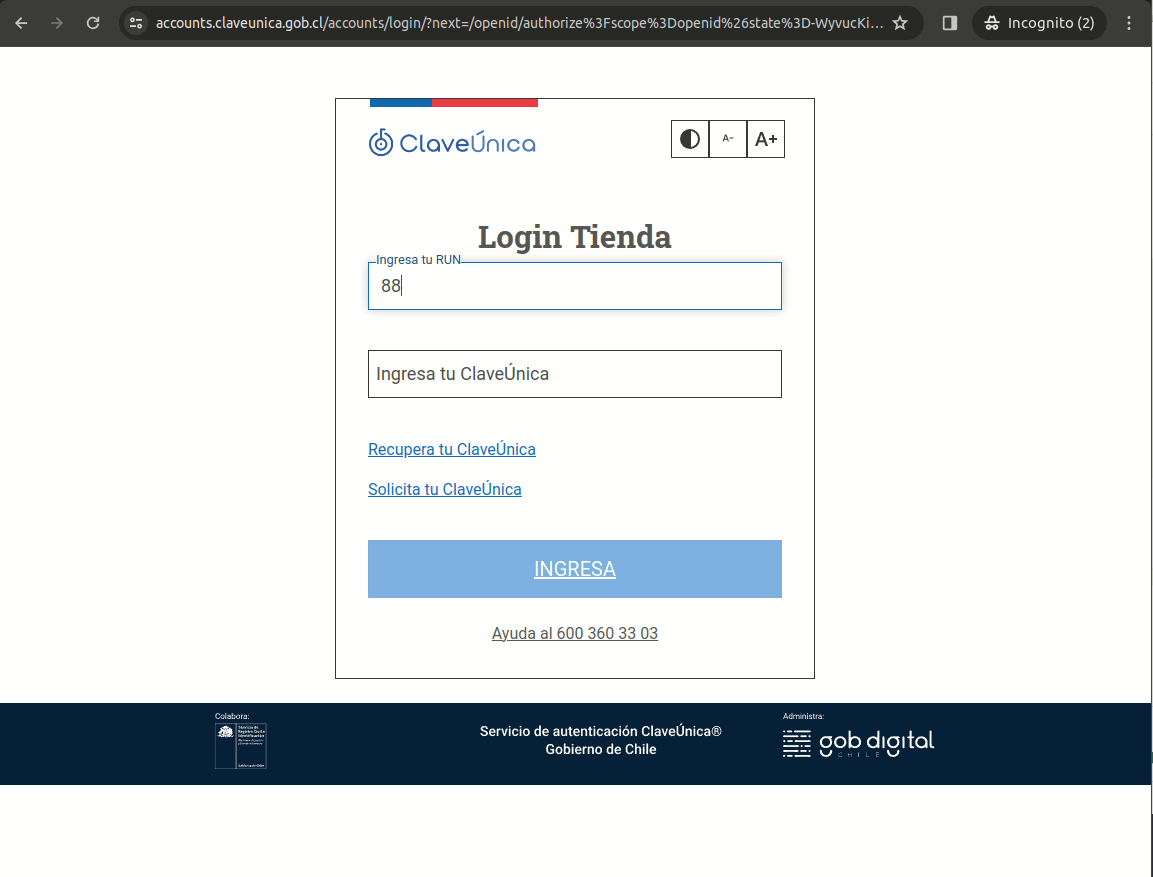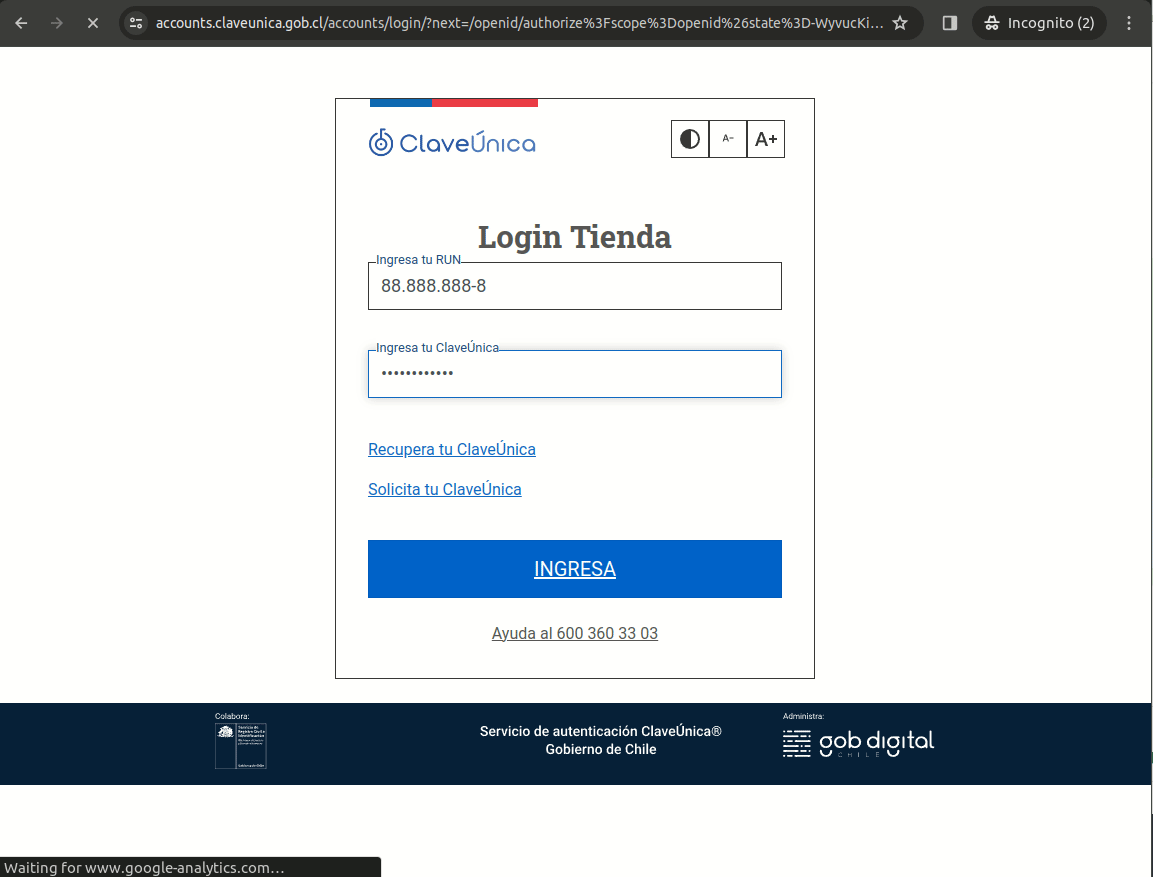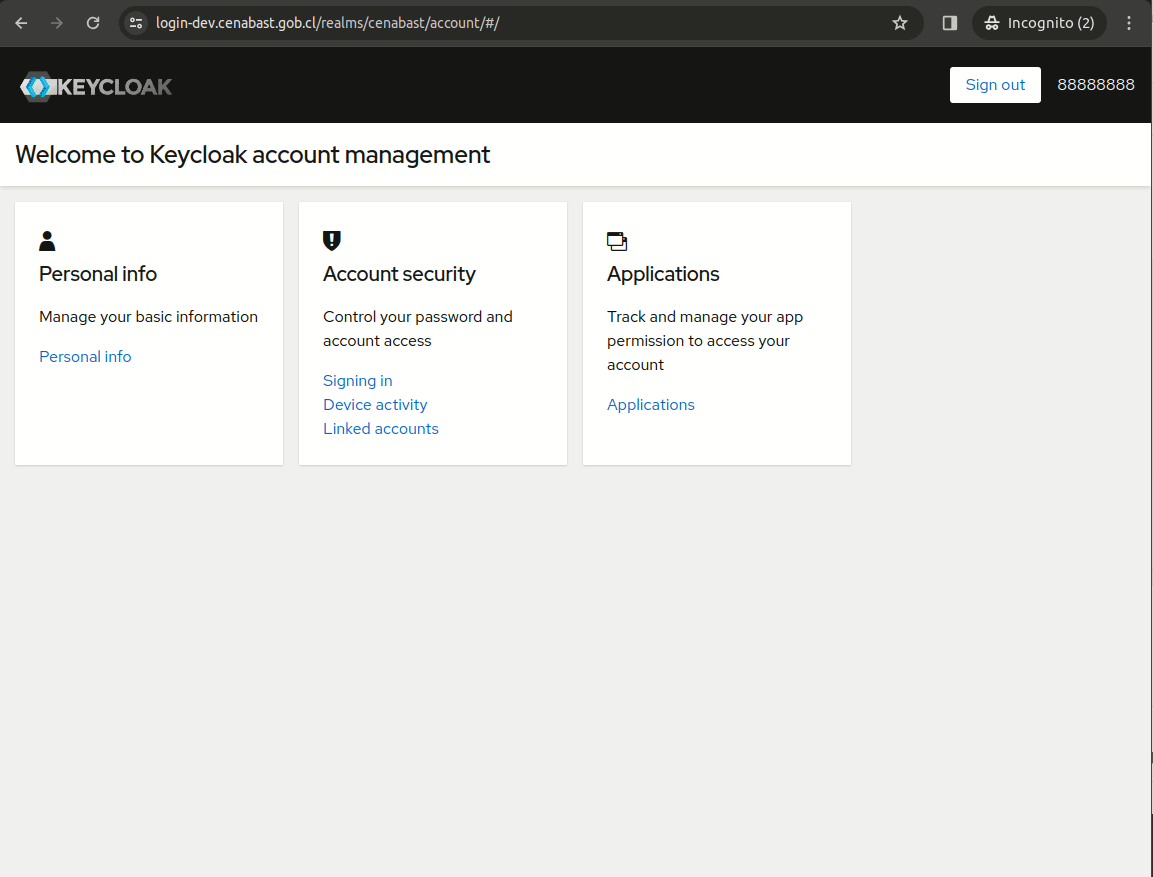
Test Login
Clave Unica test users:
RUN: 44.444.444-4 contraseña: testing
RUN: 55.555.555-5 contraseña: testing
RUN: 88.888.888-8 contraseña: testing
RUN: 99.999.999-9 contraseña: testing